DeXpose - Cybercrime Investigation
.png)
Empowering National Security Teams with Offensive-Grade Intelligence
DeXpose Cybercrime Investigation equips governments, CERTs, and cybercrime investigation units with the tools they need to trace digital identities, map criminal behavior, and proactively respond to national-level threats. Built with a focus on deep underground access, breach data correlation, and graph-powered intelligence, the module enables structured investigations into threat actors, cybercriminal groups, pedophile networks, child exploitation actors, terrorist-linked digital infrastructure, online fraud ecosystems, and compromised civilian or organizational devices. This is offensive-grade capability made available for responsible, lawful use by those defending nations, institutions, and public safety. At Tryaq, we see this not as a product, but as a mission: to empower governments, law enforcement, and enterprise security teams with data-rich, graph-powered visibility into the underground economy.
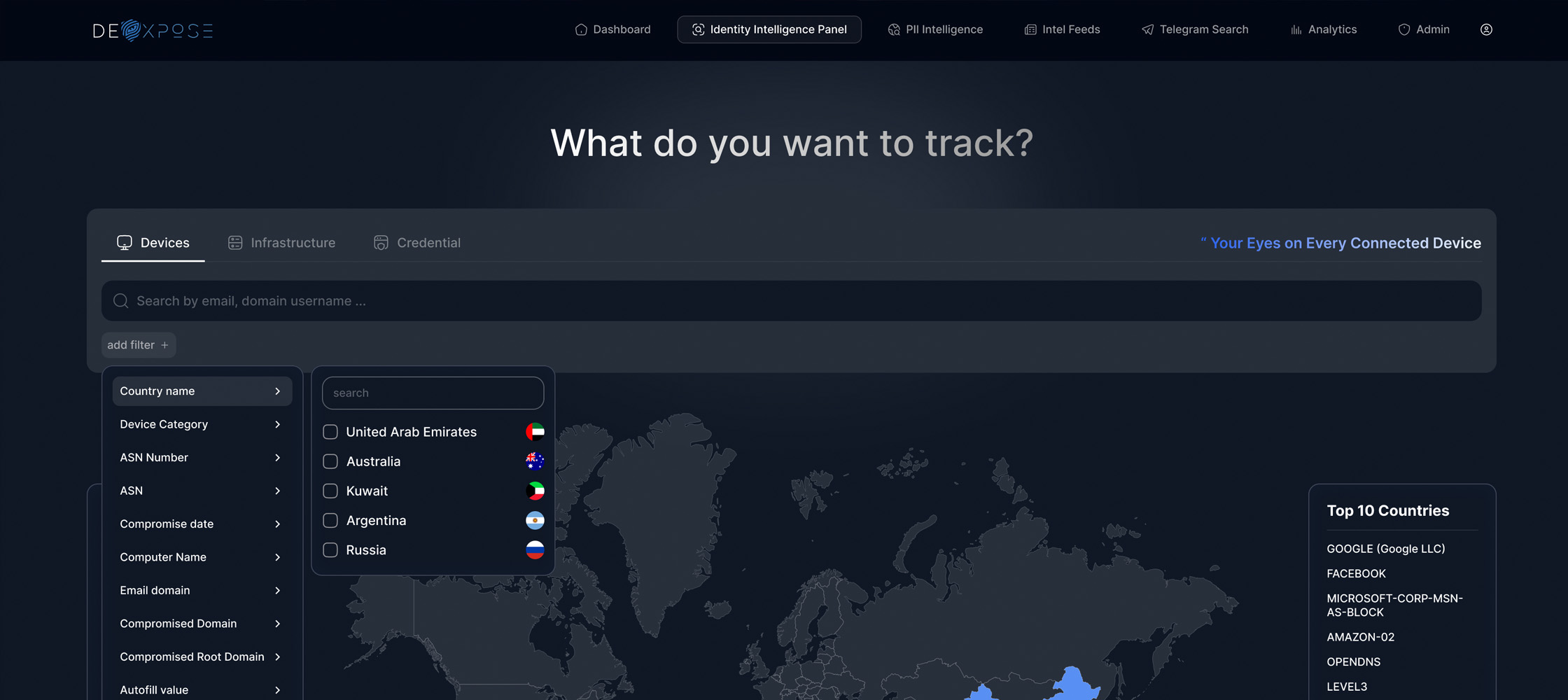
What Problem Are We Solving?
Modern cybercrime investigations are increasingly challenged by fragmented breach data, anonymous and encrypted communication platforms, rapidly shifting online identities, and the opaque nature of underground economies. Investigative teams often work with disconnected information, lack visibility into compromised infrastructure, and are unable to correlate actors across platforms and data sources.
These limitations lead to missed connections, delayed attribution, and incomplete intelligence - especially in cases involving transnational cybercrime, terrorism, or child exploitation.
How We Help Investigators & CERTs
DeXpose bridges the intelligence gap faced by cybercrime units and national CERTs by offering real-time access to compromised devices across geographies and sectors (filterable by country, ISP, or malware type), deep visibility into threat actor behavior across Telegram, dark web forums, and breached ecosystems, and structured intelligence to support identity correlation and behavioral profiling. The platform also leverages OSINT and historical threat patterns to help analysts understand how actors evolve, reuse infrastructure, and expand operations - all in a way that’s scalable, operational, and analyst-friendly.
- Graph-Based Actor Correlation
Connects aliases, usernames, emails, domains, and IPs into unified, investigative threat actor profiles. - Breach Intelligence & Behavioral Analytics
Leverages structured breach data and infostealer logs to deanonymize individuals and uncover behavioral patterns. - Underground Visibility at Scale
Monitors dark web forums, Telegram channels, and marketplaces to track criminal planning, recruitment, and activity. - OSINT-Driven Enrichment
Adds social, technical, and contextual data to investigations — supporting deeper profiling and threat modeling. - Compromised Device Intelligence
Surfaces infected machines globally, with filters by country, sector, ISP, or malware type - enabling targeted intervention.
All investigations can be conducted through a hybrid model that blends automated intelligence pipelines with manual analyst investigation - supporting both tactical leads and strategic national defense initiatives.
Other Speciality
Tryaq focuses on building intelligence-driven cybersecurity solutions that help organizations understand their digital risks, uncover hidden threats, and act with confidence. We leverage automation, threat data, and human insight to deliver scalable tools that reduce exposure and support national-level defense.
Unlock a world of innovation
Get in touch to explore solutions that enhance your defenses & expand offensive expertise.
Get in Touch